A Guide to Understanding Your Risk Mitigation Options
- May 16, 2024
- 6 min read
Updated: May 19, 2024
Risk Mitigation Condition Report
For: Acme Financial Services, Inc.
Estimated for: May 6, 2024 to May 5, 2025
This assessment is for a particular profile. A profile can be built for an entire business, a business unit, a product line, a critical business application, and any other logical or physical business entity.
How to Use Your Assessment?
This assessment explores the next twelve months of your cyber risk condition from a financial perspective. It illustrates the major cyber themes and possibilities that may present themselves to your business, based on patterns formed between historical data, your unique business profile, and the macroeconomic cyber condition.
This is your business, and the estimates for the next twelve months is just one way to think about your cyber risk condition. Your business has experienced the realities of cyber risk in a different way. This assessment should be used in conjunction with your existing observations.
This assessment is not a prediction of a pre-determined future that precludes unknown conditions and changing human motivations. Use this assessment as a target at which to aim your actions. You are the agent of your cyber resilience strategy. Take what you need from this assessment to better manage, design, and communicate your cyber resilience strategy.
Executive Summary.
Your Risk Mitigation condition is summarized in three metrics. Each metric provides an essential element in understanding and defining your risk mitigation strategy.

Since Last Quarter.
Since last quarter, your control effectiveness has improved by 50.5% and your cyber exposure has improved by 35.5%.

Special note: In most cases, cyber exposure should improve as control effectiveness improves. However, certain macroeconomic cyber risk conditions may cause cyber exposure to increase despite control effectiveness improvement.
Further Details.
Your cyber risk mitigation condition is based on a combination of your exposure profile, asset applicability, threat and impact refinement, cyber maturity, and a set of macroeconomic cyber risk conditions that further calibrate cyber incident severity and probability.
Cyber Exposure
Cyber exposure is the sum of all possible impacts each multiplied by the probability of impact, which can be further expressed as a percent of annual revenue. Your cyber exposure includes the benefit of your control effectiveness, but not the benefit of risk transfer.
Your current cyber exposure estimate is $44.3 million for the next twelve months, which can also be expressed as 1.77% of your annual revenue. To aid with making informed cyber risk decisions, cyber exposure if further divided into four exposure categories.

Question to ponder: Are you defining your risk mitigation strategy based on the riskiest cyber exposure categories.
If you are not satisfied with your current cyber exposure, then you may want to focus on the risk scenarios that contain the most cyber exposure.
Cyber Exposure Grid
Within X-Analytics, there are 110 distinct risk scenarios. Each risk scenario represents the intersection of a threat category and an asset group. Within each scenario, X-Analytics determines threat, impact (confidentiality, integrity, and availability), inherent risk, control effectiveness, residual risk, and cyber exposure.
Your total cyber exposure of $44.3 million is allocated amongst 80 applicable risk scenarios. You can use the following grid to identify your riskiest risk scenarios, your riskiest threat categories, and your riskiest asset groups.
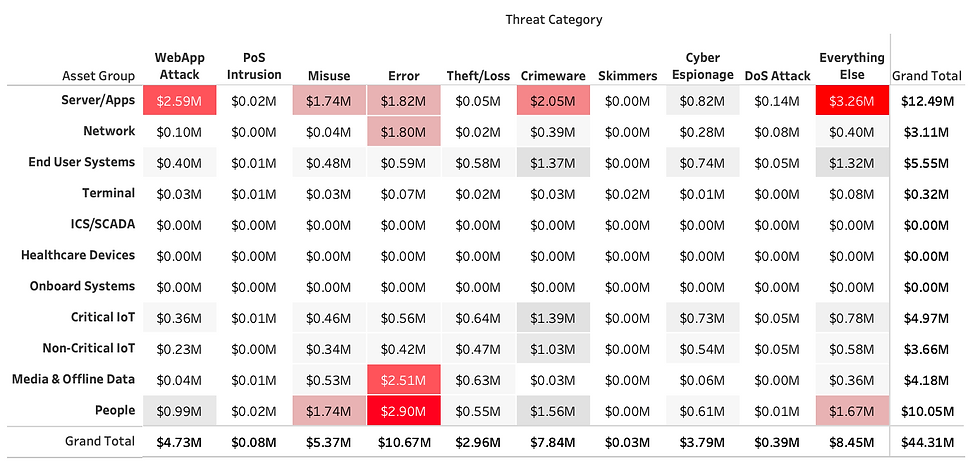
Question to ponder: Are you allocating your mitigating investments within the risk scenarios that would best improve your cyber exposure?
Use the X-Analytics risk grid to shape your risk mitigation strategy:
Your top risk scenario Unknown: Server/Apps contains 7.4% of your total cyber exposure
Your top threat category Error contains 24.1% of your total cyber exposure
Your top asset group Server/Apps contains 28.9% of your total cyber exposure
For a deeper analysis of cyber exposure by exposure category, please visit "Cyber Risk Details" within the X-Analytics application.
Control Effectiveness
Control effectiveness is the measure of how effective your overall control maturity is at reducing inherent risk. As your control effectiveness increases, your cyber exposure decreases.
Your current control effectiveness is 63.8% out of a 100% scale. When compared to inherent risk (or zero control effectiveness), your control implementation has reduced cyber exposure by $77.5 million.
Cyber Exposure (Inherent Risk) | Mitigated Exposure via Control Effectiveness | Cyber Exposure (Residual Risk) |
$121.8 million | $77.5 million | $44.3 million |
or 4.87% of revenue | or 1.77% of revenue |
Question to ponder: When you compare your cyber investments with your mitigated exposure, are you realizing a sufficient return on investment?
Control Effectiveness Grid
Within X-Analytics, there are 110 distinct risk scenarios. Each risk scenario represents the intersection of a threat category and an asset group. Within each scenario, X-Analytics determines threat, impact (confidentiality, integrity, and availability), inherent risk, control effectiveness, residual risk, and cyber exposure.
Your total control effectiveness of 64% is derived by averaging control effectiveness amongst 80 applicable risk scenarios. You can use the following grid to determine where control implementation is sufficient and to identify control implementation gaps.

The control effectiveness grid should not be used in isolation to avoid misallocation of resources. Instead, you may want to use the control effectiveness grid in association with the residual risk grid to determine prioritized mitigation and to best allocate finite resources.
Control Effectiveness in Relation to Cyber Exposure
The following graphs illustrates a relationship between control effectiveness and cyber exposure for each of your 80 applicable risk scenarios. With this graph, you can see your top risk scenarios, outliers that may require additional control effectiveness, and risk scenarios that sufficiently addressed.

To reduce your total cyber exposure, you may want to focus on your prioritized control list. The prioritized control list was developed by running a series of what-if simulations that determine how each control improves cyber exposure upon full implementation.
Prioritized Control List (Includes Multiple Frameworks)
The following table provides the top 8 prioritized controls that would best improve cyber exposure upon full implementation. This list includes controls from CIS CSC (version 8), NIST CSF (version 2.0), and Cyber Insurance Industry Recommendations (version Q2 2024).
Control Name | Definition | Current Implementation | Opportunity w/ Full Implementation |
1.Identity Management, Authentication, and Access Control (PR.AA), NIST CSF 2.0 | Access to physical and logical assets is limited to authorized users, services, and hardware and managed commensurate with the assessed risk of unauthorized access. | 50% | $6.87 million |
2.Platform Security (PR.PS), NIST CSF 2.0 | The hardware, software (e.g., firmware, operating systems, applications), and services of physical and virtual platforms are managed consistent with the organization's risk strategy to protect their confidentiality, integrity, and availability | 50% | $6.54 million |
3.Continuous Monitoring (DE.CM), NIST CSF 2.0 | Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events. | 64% | $6.07 million |
4.Asset Management (ID.AM), NIST CSF 2.0 | Assets (e.g., data, hardware, software, systems, facilities, services, people) that enable the organization to achieve business purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy. | 50% | $5.72 million |
5.Data Protection, CIS CSC 8 | Develop processes and technical controls to identify, classify, securely handle, retain, and dispose of data. | 54% | $5.36 million |
6.Security Awareness and Skills Training, CIS CSC 8 | Establish and maintain a security awareness program to influence behavior among the workforce to be security conscious and properly skilled to reduce cybersecurity risks to the enterprise. | 71% | $3.43 million |
7.Risk Assessment (ID.RA), NIST CSF 2.0 | The cybersecurity risk to the organization, assets, and individuals is understood by the organization. | 60% | $3.35 million |
8.Data Security (PR.DS), NIST CSF 2.0 | Data are managed consistent with the organization's risk strategy to protect the confidentiality, integrity, and availability of information | 70% | $3.34 million |
Special Note: The prioritized control list should not be viewed in aggregate since there is a chance that overlapping benefit exists among the top 8 controls. For example, control #1 may include mitigating components that overlap with control #4. If you were to add the benefit of the two, then you would be overstating the total benefit.
To understand prioritized risk mitigation without the potential of benefit overlap, please visit the "X-Analytics Actions" section of this report.
X-Analytics Actions
The X-Analytics Actions is a list of mitigating actions that effectively reduce cyber risk. The X-Analytics Research Team created the X-Analytics Actions as a way to categorize mitigating concepts amongst multiple control frameworks that eliminate the potential of overlapping benefit.
Currently, you have implemented 61.8% (Moderate mitigation) of the X-Analytics Actions by implementing one or more cybersecurity frameworks within your organization. Your X-Analytics Actions score is based on averaging your implementation amongst the 32 mitigating actions.
X-Analytics Actions with Current Implementation Value
The following graph represents the full list of X-Analytics Actions and your current implementation of each action. Your X-Analytics Actions score is based on averaging your implementation amongst the 32 X-Analytics mitigating actions.

You can use the above graph to identify gaps in your mitigation plan and to realize where you have achieved success within your mitigation plan.
X-Analytics Actions with Current Implementation Value and Exposure Improvement Opportunity
The following graph represents the full list of X-Analytics Actions with your current implementation of each action, and the remaining cyber exposure improvement opportunity with full implementation. X-Analytics determines the cyber exposure opportunity value by running a series of what-if simulations to understand the delta between current cyber exposure and "what-if" cyber exposure.

Special Note: You may notice that the least implemented X-Analytics Actions do not offer the best cyber exposure improvement opportunity. This is due to the fact that X-Analytics Actions are not equal in risk reducing quality based on your risk profile, your thread condition, and the macro cyber economic condition.
Question to Ponder: Are your current investments aligned to the X-Analytics Actions that would best improve your cyber exposure?
If you are not satisfied with your current cyber exposure, control effectiveness, or implementation of the X-Analytics Actions, then you may want to use the "X-Analytics Prioritized Mitigation Plan".
The X-Analytics Prioritized Mitigation Plan
The X-Analytics Prioritized Mitigation Plan is a prioritized list of mitigating actions that would best improve your cyber exposure. The prioritized list was developed by running a series of what-if simulations that determine how each mitigating action improves cyber exposure upon full implementation. Inside of each mitigating action is a reference to CIS CSC (version 8), NIST CSF (version 2.0), and Cyber Insurance Industry Recommendations (version Q2 2024) controls.
The following table provides the top 8 prioritized mitigating actions that would best improve cyber exposure upon full implementation.

Special Note: As additional frameworks are introduced with X-Analytics, the associated guidance will expand.
If you focus on the top 8 X-Analytics Actions, you could reduce $18.3 million from your current cyber exposure. This would represent a 41% reduction in risk.
For additional insights, please visit the X-Analytics Report Center.
Closing Remarks
Your cyber risk transfer condition is summarized in three metrics. Each metric provides an essential element in understanding your risk transfer strategy.
Cyber Exposure
1. Your current cyber exposure is $44.3 million (or 1.77% of revenue).
2. Your top exposure category Interruption contains 76.3% of your total cyber exposure
3. Your top risk scenario Unknown: Server/Apps contains 7.4% of your total cyber exposure.
Control Effectiveness
1. Your current control effectiveness is 63.8% (or Substantial effectiveness).
2. Based on your current control implementation and earned control effectiveness, your mitigated exposure is $77.5 million.
3. If you fully implement your top control recommendation Identity Management, Authentication, and Access Control (PR.AA), you could further reduce your cyber exposure by $6.87 million.
X-Analytics Actions
1. Your current implementation of the X-Analytics Actions is 61.8% (or Moderate mitigation).
2. Penetration Testing and Remediation is your most prioritized action, it is currently implemented at 48%, and it could further reduce your cyber exposure by $2.52 million upon full implementation.
3. If you implement your top 8 X-Analytics Actions, you could reduce your risk by 41%.



Comments